As the attacks increase, incident response plans become more vital to a company's cyber defense. Many companies are affected by cyber breaches, so implementing a well-structured Incident Response Lifecycle is a great way to mitigate cybersecurity incidents.
What is an Incident Response?
Incident response is a process used to respond to a cyberattack in an organization. The data breach and cyberattacks can potentially affect the customers, brand value, and intellectual property of the company resources and time. An incident response aims to reduce the violation of security policies and recommended practices.
The Incident Response is managed by an organization's Cyber Incident Response Team (CIRT), incorporated with the security, IT staff, legal members, human resources, and public relations departments.
Incident Response Lifecycle
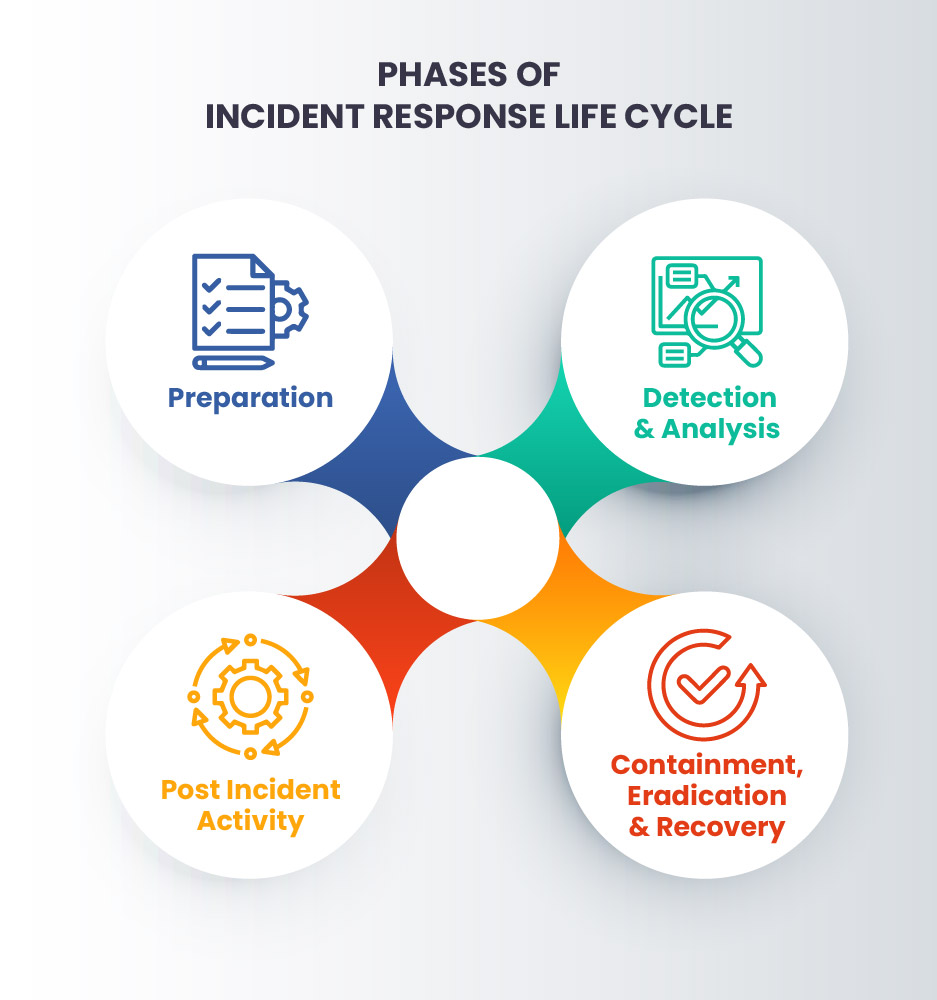
The Incident Response Lifecycle is a step-by-step process of responding to the security incidents such as security breaches, unauthorized access, server downtime, etc. In general, there are four phases of an Incident Response Lifecycle:
Preparation: Preparation is the best way to overcome cyberattacks. This phase involves discussions and preparation on how to handle and prevent security incidents. The CIRT and IT staff are responsible for handling potential incidents with the best response strategy, tools, and controls.
Detection and Analysis: The second phase is to detect and determine step-by-step instructions for handling the security incident and quickly start with a response to reduce impact and cost.
The following are detection and analysis techniques used as a plan of action:
Penetration Testing
Vulnerability Assessment
Frequent checks
Containment, Eradication, and Recovery: The third phase is Containment, which divides the affected systems from the network to reduce the incident's damage. During the eradication phase, the incident handler focuses on identifying the root cause of the incident. Then the affected systems are removed from the production environment to minimize data loss.
The Recovery phase is the foremost step in the Incident Response Lifecycle, which includes restoring systems from backups, rebuilding the system from scratch, replacing compromised files, changing passwords, installing patches, and strengthening the security.
Post-Incident Activity: This is the most important phase of the Incident Response Lifecycle. The post-incident activities, such as lessons learned, help to educate and enhance the skills to improve the efforts for future incidents. Preparing incident documentation and performing an analysis of the incident will be the guide for the future.
The Incident Response Lifecycle is defined in many ways, in which the National Institute of Standards and Technology (NIST) has developed an incident handling framework. Organizations can build their Incident Response Lifecycle or can implement the existing frameworks.
Incident Handler with InfosecTrain
InfosecTrain offers an instructor-led training program on Certified Incident Handler V2 accredited by EC-Council. Our well-experienced trainers help you to achieve the extensive skills required to define security incidents and implement the Incident Response plan accordingly. Check out our course to know more.